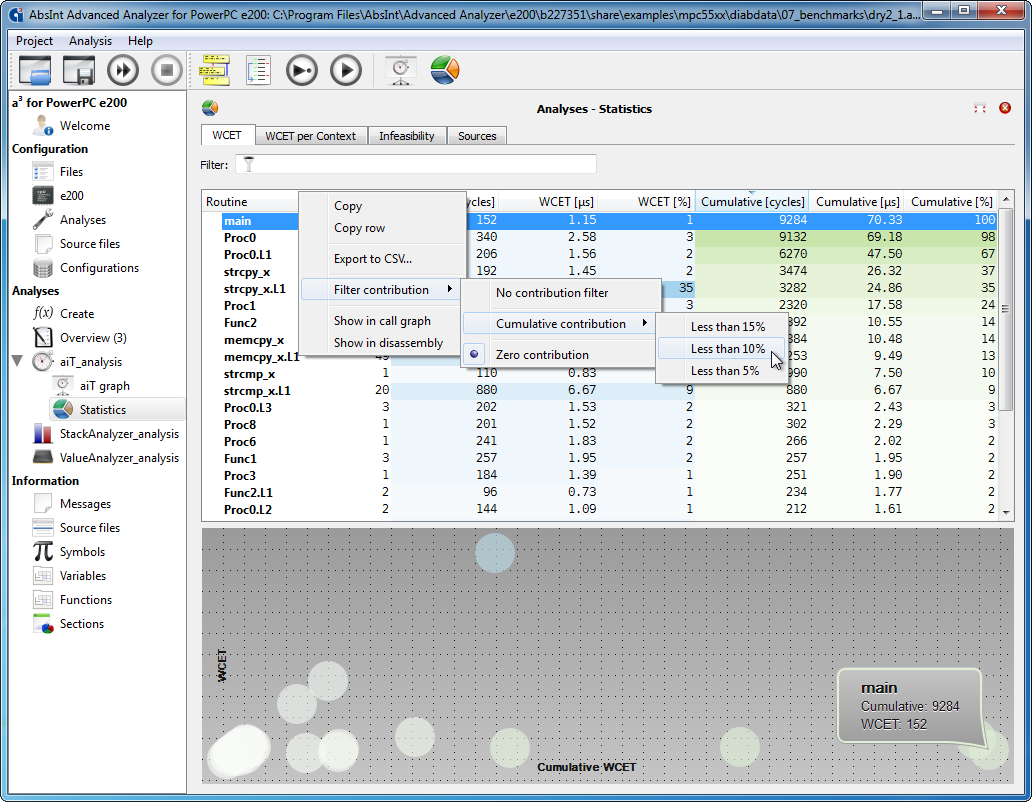
 Filters in Statistics views |
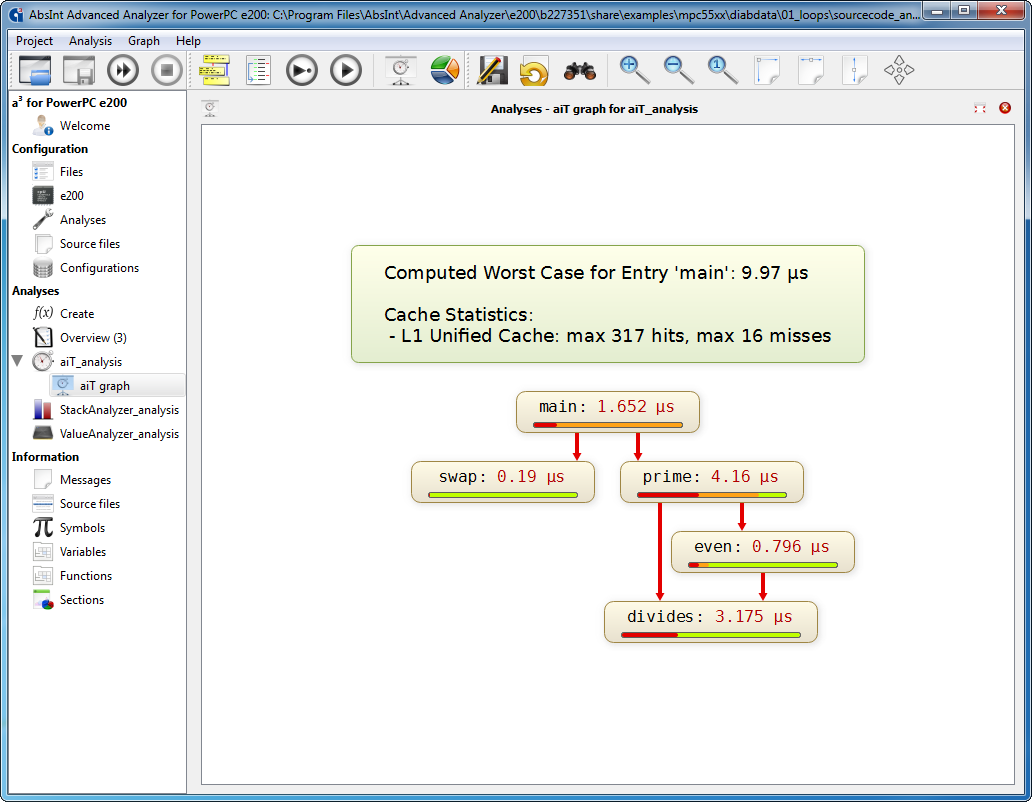 Improved call graphs |
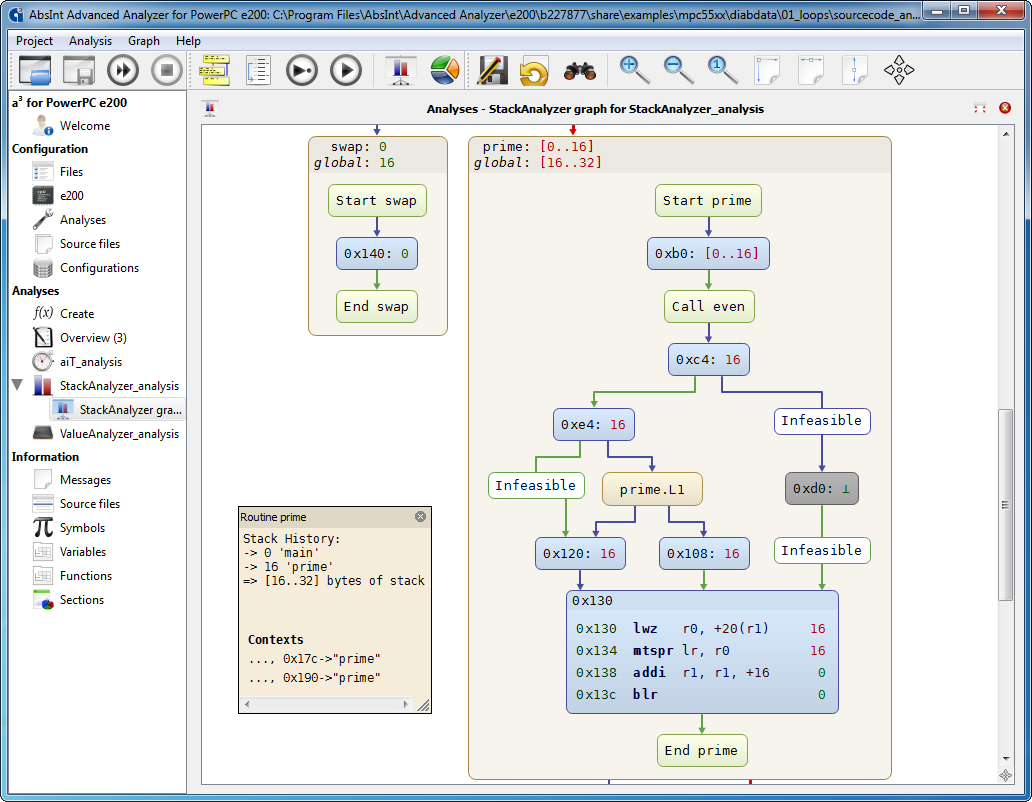 Improved control-flow graphs |
Targets
- aiT for Am486 now supports write-back enhanced IntelDX4.
- aiT for TriCore now supports TC1782 and TC1784.
- a³ for MPC603e has been renamed into a³ for e300.
- a³ for MPC55xx and a³ for MPC56xx have been merged into a³ for e200.
- aiT for e200 now supports MPC5777M.
- a³ for ARM now supports the IAR compiler.
- StackAnalyzer and ValueAnalyzer for ARM now support the NEON extension.
Qualification Support Kits

- QSKs for MPC603e and MPC55xx have been renamed to QSKs for e300 and e200, respectively, following the corresponding changes to the tools.
- New QSK for aiT for e200: compiler-specific package for DiabData 5.9.1.0.
- New QSK for aiT for MPC5xx: compiler-specific package for DiabData 5.2.1.0.
32-bit Windows support
Starting with this release, packages for 32-bit Windows are no longer automatically dispatched, but are only available on request. Please contact support@absint.com if you are still using 32-bit Windows.
AbsInt Launcher
The owner of the cookie section in the XTC file is now alauncher.
Known issue
When exporting projects via “Project” → “Export”, annotations of the following form are omitted:
global "<attribute name>" = "<attribute value>";
- All-new graph visualization with numerous improvements.
- The GUI now allows specifying a default incarnation bound of recursions for the stack analysis. The default incarnation bound is only used for a recursion in case no other annotation is given. This setting can be found under “Analyses” → “Common” → “Stack analysis”. The default is 1. The fallback can be deactivated by setting it to unlimited. If the stack analysis uses the default incarnation bound, a warning will be issued so that potential issues can be detected.
- Similarly, the GUI now allows specifying a default loop bound and default recursion bound for the timing analysis. These settings can be found under “Analyses” → “Common” → “Path analysis”. The default for each is 4. It is possible to deactivate these fallbacks by setting them to unlimited. The default recursion bound is only used for a recursion in case no other annotation is given. The default loop bound is only used for a loop in case the loop analysis cannot detect any bound and no other annotation is given. If the path analysis uses any of these default values, a warning will be issued so that potential issues can be detected.
- Improved WCET results visualization in Statistics view. The tree view can be filtered by cumulative contributions of routines and by call depth.
- PowerPC: the GUI allows specifying the values of SDA14 through SDA17 as used by the HighTec GCC.
- In the Source Files view, the names of the files that have not been found (gray entries) can now be copied.
- Fixed handling of non-Latin-1 characters in recently opened projects dialog.
- Extend reference syntax for ResultsCombinator to address additional starts.
- CSV export now conforms to system locale.
- Fixed known issue from release 14.04: example projects opened as a temporary working copy can again be saved to directories containing non-temporary data.
AIS
- The global loop-iteration default annotation was removed in favor of the new GUI setting. It is still parsed but no longer has any effect.
- Added support for the annotation
instruction <pp> target is not analyzed and violates calling conventions;
- The annotation
instruction <pp> overwrites areais deprecated. Use the AIS2destroyannotation instead. EVA-based value analyzers will ignore theoverwritesannotation. - The AIS2
destroyannotation is now applicable to arbitrary address ranges and arbitrary access width ranges except width == 0. - Unrecognized keywords are reported in a more understandable way by the AIS parser.
Decoding
- Improved robustness against invalid symbol table entries (e.g. wrong routine sizes).
- ARM:
- Added support for the NEON extension.
- Added support for the IAR compiler.
- C16x: improved detection of the Tasking VX toolset.
- PowerPC:
- Added support for the Lightweight Signal Processing (LSP) APU extension.
- Added support for decorated load-store instructions used in e200 architectures with decorated storage memory controller (DSMC) as found in MPC5777M.
- FR81: improved reading of line information.
- TriCore:
- Improved switch table decoding.
- Improved guessing of the context save area.
- Improved handling of space optimized executables generated by Tasking.
- V850:
- Improved switch table decoding for GHS compilers.
- Improved support for recent GHS compilers (6.1.4).
- Improved switch table decoding for switch tables that are implemented
via 32-bit displacement
jmpinstructions.
New value analysis framework
The PowerPC, C28x and FR81 targets have been ported to a new value analysis framework called EVA. Other targets will follow suit in future releases.
EVA features a number of changes vs. the original value analyzer. Certain annotations will need adjustments, e.g. interproc flexible specifications and some value analysis specific annotations.
The most important changes are:
Unified loop and value analysis
There are no longer multiple loop analysis rounds followed by a final value analysis round, but rather only one combined analysis phase. This affects the output messages and reports. For example, in XML reports there will be no separate analysis contexts for loop and value analysis, and the XML schema was adapted for the context-sensitive value analysis results.Different mapping computation
The parametermax-unrollno longer has any effect on the value analysis. Instead,default-unrollnow specifies the maximum unrolling limit for all loops. This change was necessary to unify loop and value analysis and optimize the performance for projects with infinite call-string and large unroll settings. This means that when complete unrolling is desired, a large enoughdefault-unrollvalue must be specified. The same holds for loop-localmax-unrollspecifications.Stack analysis inlines loops
Instead of regarding loops as separate routines, the new stack analysis regards them as part of the surrounding routine. This implies that the stack height inside loops will no longer start at 0 but at the current stack height in the surrounding routine. Stats and reports will no longer list loops as separate routines for stack analysis.Improved interactive value analysis
The interactive value analysis can be invoked not only for instructions but for any block (in particular, the call nodes) as well as for routines. This enables a better overview of the cumulative effect of that block or routine on the value analysis results. For blocks with instructions and routines, one can use the interactive value analysis to generate AIS annotations. The generated annotations for instructions, normal blocks and routines include bothenter withandexit withannotations. For targets with speculative execution, the speculative value analysis results are displayed in a secondary tab.Higher precision
- The branch splitting has been greatly improved, and covers more compare and branch scenarios.
- Better handling of imprecise memory reads/writes.
- Improved computation of possible ranges of loop variables.
- Improved widening of intervals.
Optimized memory usage
Reduced memory consumption by storing analysis information at fewer program points.Optimized speed
The analyzer will now compute the fixed-point result in a single iteration if the mapping allows it (infinitemax-length, full unrolling, and no recursions).Expression evaluation
Values are truncated to target register sizes. e.g. if-inf..infis put into a 32-bit user register, it will be 32-bit full range.Annotation changes
instruction/routine <pp> area containsis now ignored, use theentered withannotation insteadinstruction <pp> overwrites areais now ignored, use the new AIS2destroyannotation instead
Stack-transparent routines
Stack frame creation/destruction/restoration routines are marked as stack-transparent during decoding. If a routine is marked as stack-transparent, it uses the stack frame of the caller. Stack effect annotations cannot be applied to stack-transparent routines.
Other stack and value analysis updates
- For external routines and unresolved computed calls, the default assumption has changed to be that the calling conventions hold and the called routines have no stack effect. The analyzer will issue a warning every time such an assumption is actually made, along with a suggested annotation for the program part in question.
- Faster analysis for binaries with many sections (e.g. when each function is in a section of its own).
- Faster stack analysis for programs with complex recursions.
- The analyzer now outputs the annotations generated for later iterative decoding phases to the text and XML report files.
- The analyzer will no longer inform about loops that seem to have fewer iterations than annotated as long as it is not an error and has no impact on analysis precision and time.
- Now ignoring
area containsannotations for speculative accesses. - ARM: added support for the NEON extension.
- PowerPC: improved handling of 64-bit compare instructions used in 32-bit PowerPC code. Correct execution of 32-bit semantics is now assumed, and a corresponding info message is issued.
- TriCore:
- Improved handling of syscall trap routines.
- Improved loop analysis for 64-bit move instructions.
Cache and pipeline analysis
- Interactive pipeline analysis visualization now available for individual instructions in addition to basic blocks.
- ARM Cortex-R4F: improved pipeline model for the FPU/VFP.
- MPC7448: implemented support for 16-byte burst instruction fetches.
Path analysis
All path analysis variants now support timing specifications for loops.
Visualization and reporting
- Improved HTML reporting for architectures with multiple stacks.
- Changed the XSD for the output of context sensitive value analysis results like access information.
- Fixed reporting of configuration settings in report files when configurations are used.